Fixing Open Source Vulnerabilities in Azure Dev Ops
Once your python app is created and deployed, its time for you to relax and take a chill pill. Or wait, is it?
After making and deploying a new web application, every time you receive a new feature request or your team fixes a potential bug, you will need to test and deploy the application again.
Here is where Azure Dev ops can help you. Create a Azure pipeline in your Azure Dev Ops organization so that every time you push into the GitHub main branch, your code automatically is tested and the builds run to deploy your web application.
Now, have you used several open source libraries in your project? That may lead to open source vulnerabilities and security risks. Thankfully, there are extensions available to help you out.
No worries! The WhiteSource Bolt extension for Azure DevOps will detect open source vulnerabilities and suggest fixes as well!
So, in this article, we will build a sample Python app to see how we can identify open source vulnerabilities in our project with the WhiteSource Bolt for Azure DevOps extension.
Agenda
- Create and deploy a web app using Azure.
- Create a CI pipeline with Azure DevOps to link our GitHub Repo.
- Integrate WhiteSource Bolt extension with Azure Devops to fix open source vulnerabilities in our project.
Create Azure Web App
Go to Resource Groups :

Go to Web App and enter the details of your app.

After filling in, wait for it to get deployed. It will show on the home screen :

The app is deployed here : https://pythonwebapplication.azurewebsites.net/
Initially, it will show a page stating the deployment is successful.
Azure Dev Ops
To get started with Azure DevOps, you will need to first sign in and create a new organization.
Create a new project and select visibility as public or private :

You will come to this screen :
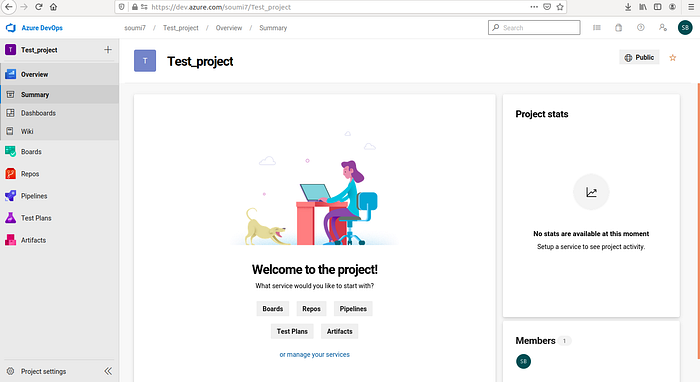
You can push your existing code on a GitHub repository to Azure DevOps.
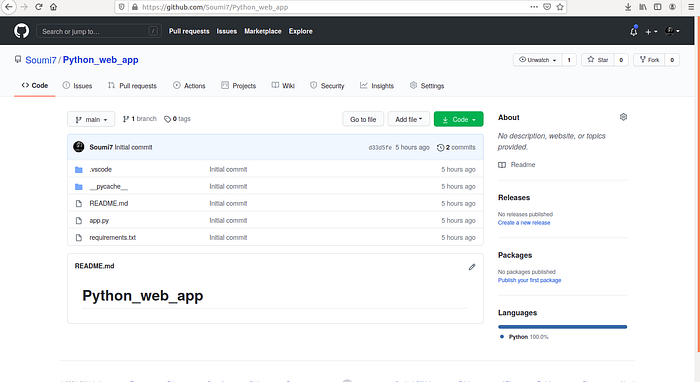
Create a sample GitHub repository similar to this or write your own code. This one is just for testing purposes.
Navigate to
Repos:
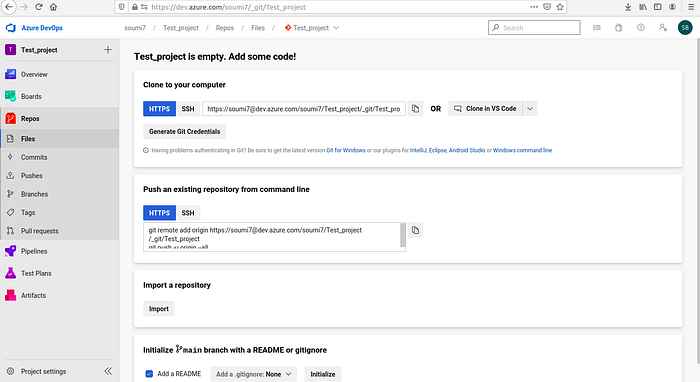
Generate the Git Credentials.
Now open up the terminal on your machine and clone the repo using this link using this git clone.
git clone https://github.com/Soumi7/Python_web_app.gitNow open up the folder with VSCode :
code Python_web_appI have create a simple flask app with the following code :
Next, we need a requirements.txt file for the dependencies. Here, as this is a test project, the only dependency is Flask:
Flask==1.1.2Run and debug the python web app. Once it runs locally, connect it to azure Devops.
Type this in the VSCode Terminal :
git remote set-url origin https://soumi7@dev.azure.com/soumibardhan7/Test_project/_git/Test_project Push the code :
git push -u origin --allYou could also directly connect your existing GitHub repository by providing the link.
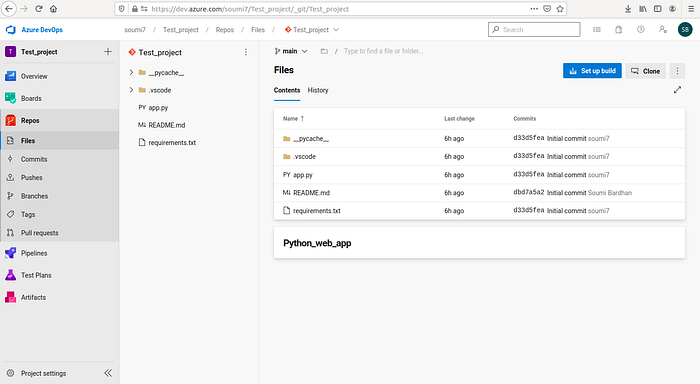
Now navigate to Pipelines and click on Create PipeLine:

Click on Azure Repos Git :

Select a repository : Test_project

Select Python to Linux Web App on Azure

Next, select the web app name :
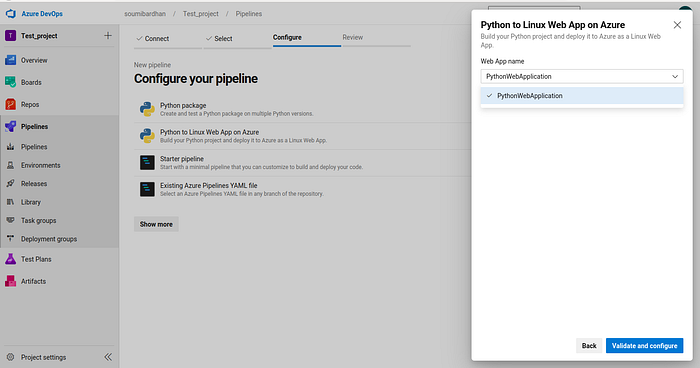
Now you can see the YAML file. Click Save and Run.

So, everytime you push to the main branch on the GitHub repository, the builds will run and the web application will be deployed only if all the builds run successfully.

See the status of the pipeline and jobs :

The app should have successfully deployed:

Now, navigate to the Azure website to see if the site is running successfully. The pipeline looks like this after the builds run successfully. The pipeline looks like this after builds run successfully :

So you have successfully created your Azure pipeline and everything is running smoothly. But, wait! You have used several open source libraries and frameworks to create the application!
WhiteSource Bolt Azure Dev Ops Extension
Open Source vulnerabilities pose serious security risks to application security. In 2021, everyone is aware how important security is. These vulnerabilities can be data breaches, malware injections etc.
To assist with this, I use White Source Bolt for Azure DevOps. If you are using Azure DevOps, you have already created a Azure pipeline for continuous deployment of your web application. WhiteSource Bolt is a free extension that can be integrated with Azure pipelines to identify potential open source vulnerabilities in your application. It also provides fixes.
It can also provide feedback in real-time on open source components that are added to your build. If the component is found to be vulnerable, a report is generated with suggested fixes. It catches vulnerabilities in existing components.

Let’s look at how to use it:
Start by installing the extension from the Visual Studio Marketplace. Then, once it’s set up, select your organization. I have already installed the extension before, so it shows this message:

After selecting the Azure DevOps Organization, you see this screen :

You need to connect your organization to an Azure Active Directory. Go to Organization Setting -> Azure Active Directory and Select a directory.

This screen pops up :

Now lets look your Azure Dev Ops organization dashboard. This is what it looks like, with one existing project — Test_project.

Navigate to Pipelines -> WhiteSource Bolt. Enter your details to create a WhiteSource Essentials Account to start your 30-day free trial :

You receive a link via mail to create your white source account :

Now, login :

Generate your Azure DevOps plugin Activation key :

A message for successful account creation is displayed :

Go to your Pipeline, select the pipeline and click Edit :

Go to the Tasks section :
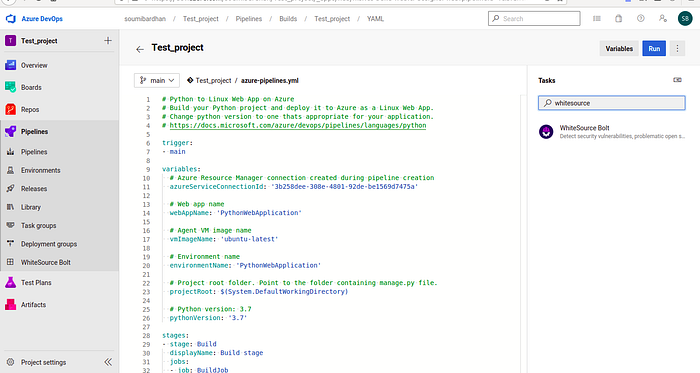
Select WhiteSource Bolt :
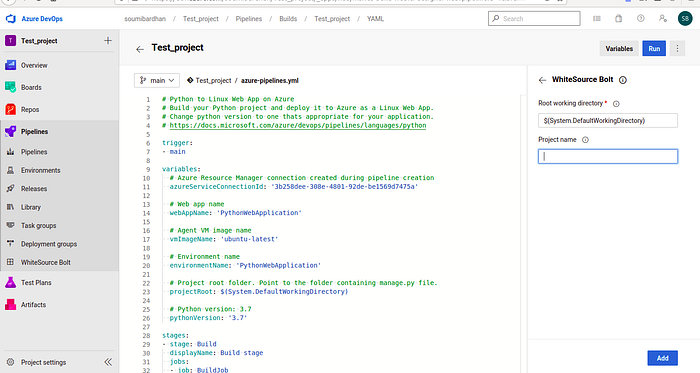
Add the snippet of code to the end of the build stage to add the task :
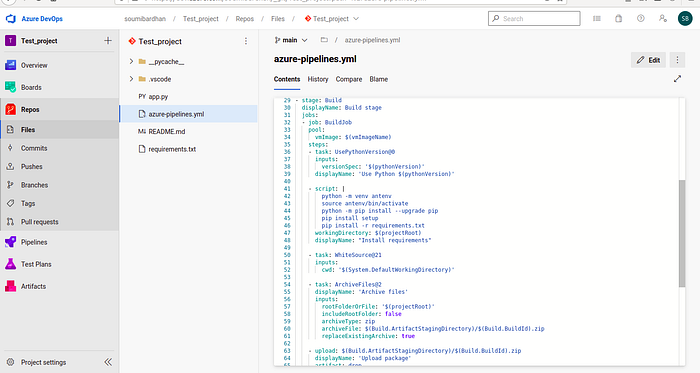
Now go to Pipelines and select the run for which you want to check the WhiteSource Bolt Open Source Risk report :

It shows us the inventory, outdated libraries, security vulnerabilities and license risks. The report shows there are 0 risks right now :

As we have only one dependency in our requirements file, Flask, which is the latest updated version, no vulnerabilities are detected. This tells us our project has no risks.
Lets see what happens if we have some other deprecated frameworks in our dependencies.
Make these changes in the requirements.txt file.

Wait for the pipeline to complete deployment :

After the build runs, check the WhiteSource Bolt Open Source Risk Report:
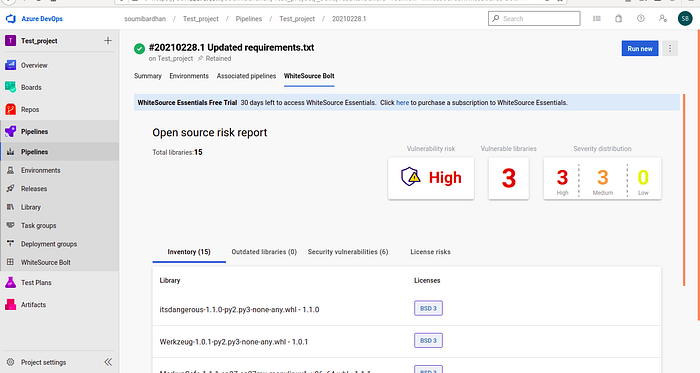
You can see the Vulnerability risk is High. There are 3 vulnerable libraries. The severity distribution is also visible.
Select the Security vulnerabilities tab :

This shows all the vulnerabilities, libraries and suggests fixes. Here is one of the suggested fixes for the cryptography library :

This is another suggested fix, this time for httplib2 library:

You can also look at the license risks :

Lets update cryptography to version 3.3.2 as suggested by the WhiteSource Bolt extension risk report fix. The
requirements.txtfile will now look like this :

Commit and Push to ‘main’ branch. This will trigger the pipeline to run the builds. Check the WhiteSource Bolt Risk Report now :

You can see the vulnerability risk is still High but the vulnerabilities libraries have decreased from 3 to 2. In the severity distribution, 1 is high severity and 2 are medium.
That means the suggested fix worked!
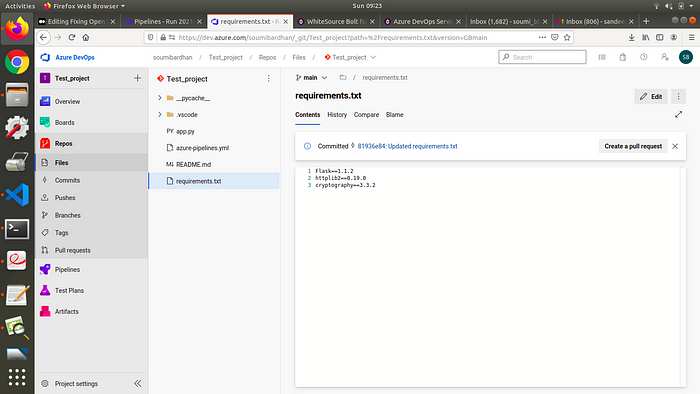
Lets update httplib2 to 0.19.0 as suggested by the fix :

Updated
requirements.txtfile will look like this :
Commit and push. This will trigger the build again. Once it completes, look at the Open Source Security Report under the WhiteSource tab :
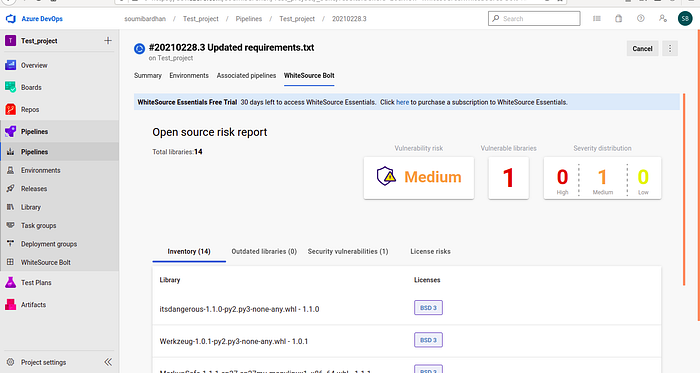
You can see, the vulnerability risk has reduced to medium now, and the number of vulnerable libraries have reduced to 1.
